Securing the Click: Why Endpoint Phishing Protection is Non-Negotiable
When phishing bypasses email gateways and firewalls, the endpoint is your last line of defense.
In today's threat landscape, the phishing defenses that worked yesterday aren't enough to stop the attacks of tomorrow. Endpoint phishing protection doesn't replace your existing controls—it strengthens them and provides a true last line of defense.
The Critical Gap in Modern Defenses
In today's threat landscape, the phishing defenses that worked yesterday aren't enough to stop the attacks of tomorrow. Most enterprises rely on a layered security stack—secure email gateways (SEGs), firewalls, and endpoint suites—to keep threats out.
But there's a critical gap that many organizations still miss: phishing protection and malicious link management directly at the endpoint, where the click actually happens.
Email and network tools are essential. Yet phishing links continue to slip through, especially as attackers move beyond email into social media, collaboration platforms, and search ads. Endpoint phishing protection doesn't replace your existing controls—it strengthens them and provides a true last line of defense.
Phishing: A Persistent and Expensive Threat
Phishing remains one of the most successful ways for cybercriminals to compromise enterprise environments. According to the 2024 Comcast Business Cyber Threat Report, phishing represented the highest attack vector, with 2.6 billion interactions leading to credential theft and malware delivery. The average cost of a breach initiated by phishing is $4.88M (IBM Cost of a Data Breach 2024).
Phishing attacks often arrive as emails or messages that:
• Trick users into clicking malicious links
• Deliver infected attachments
• Harvest credentials or sensitive information
SEGs and network security tools do a good job of filtering known phishing emails and blocking known-bad sites. But they are still limited by signatures, static rules, and pre-existing threat intelligence. That leaves organizations exposed to:
• Zero-day phishing campaigns
• Links that turn malicious after delivery
• Attacks coming from "trusted" or compromised domains
• Threats delivered outside corporate email entirely
This is where endpoint-level phishing protection becomes essential.
The Blind Spot: Phishing Exposure Outside Your Perimeter
Corporate networks are increasingly blind to phishing exposure that happens outside managed email and networks.
Attackers now routinely weaponize:
• Search engine ads leading to fake login pages
• Comment sections on high-traffic sites like Reddit or X
• Social media messages and posts on platforms like LinkedIn
• Links shared in collaboration tools such as Slack, Teams, or shared docs
These links may never pass through your SEG or perimeter firewall, but they absolutely reach your employees' browsers.
Malicious Link Management: Closing the Gap at the Endpoint
Even when users aren't targeted directly via email, malicious links can still show up everywhere they work and communicate.
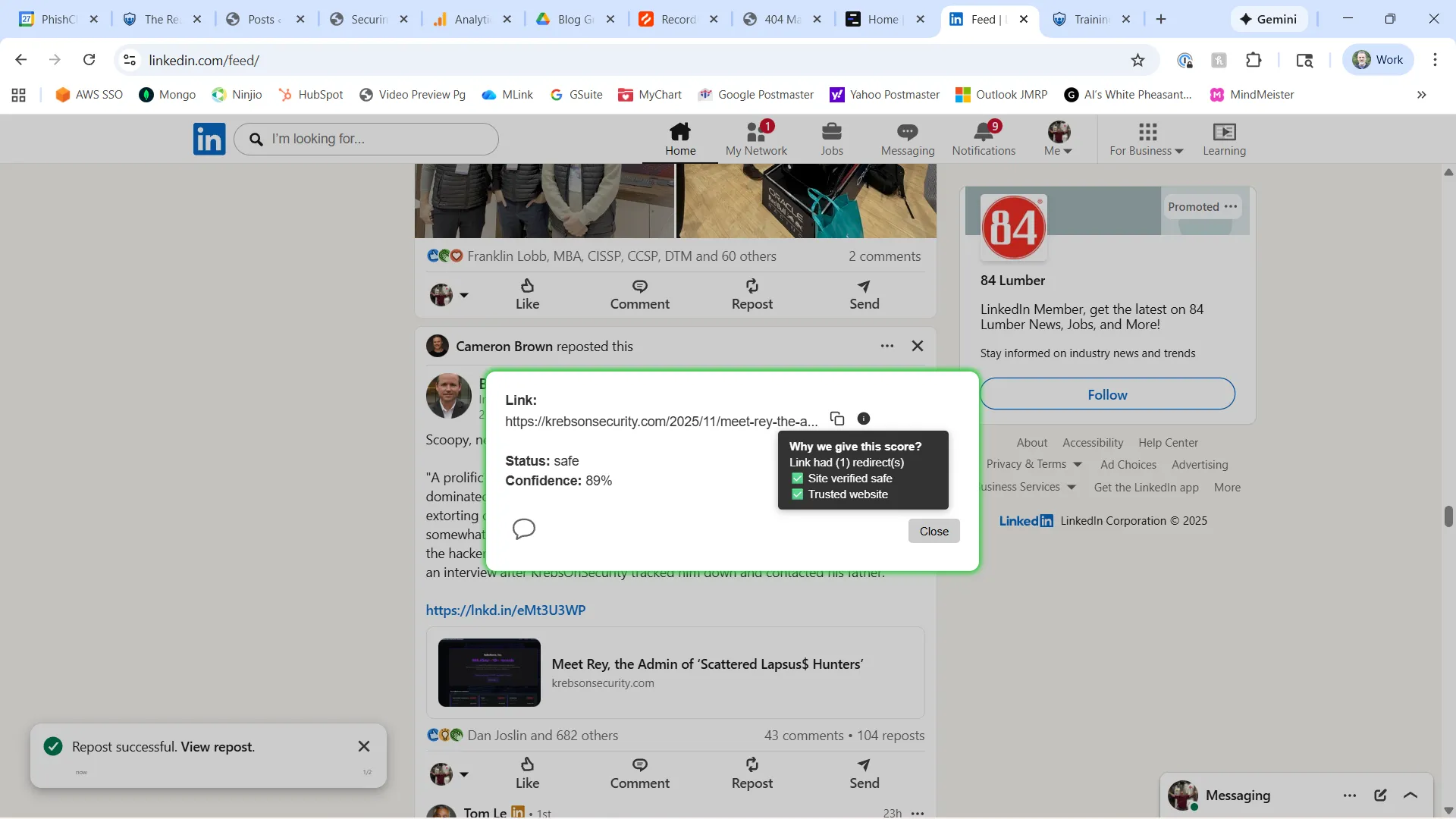
Modern malicious link management at the endpoint:
• Scans URLs in real time when and where the user encounters them
• Unshortens links and resolves every redirect to the final destination
• Analyzes dynamic content, not just static reputation
• Scores and classifies risk, enriching your security stack with actionable data
As a cloud-native solution, endpoint link management can:
• Provide visual, in-context safety indicators (green/yellow/red) directly in the browser
• Operate inline with normal business workflows, without breaking productivity
• Feed real-time intelligence back into firewalls, SEGs, and SIEM/SOAR platforms to block active campaigns across the enterprise
The result is a continuous layer of protection that follows the user—not just the inbox.
Adding Phishing and Link Protection to the Endpoint
Endpoint protection operates at the device level, monitoring user activity, files, and network interactions. When you embed phishing and malicious link protection into that layer, you gain three major advantages.
1. Real-Time Protection and Response
Endpoint platforms with integrated phishing defense use real-time threat intelligence and behavioral analysis to stop attacks as users interact with links.
They can:
• Scan every URL exposed to the user, regardless of delivery channel
• Immediately warn or block when a link leads to a phishing page or malicious site
• Correlate events across users and devices to identify common attack vectors faster
This means your organization still has a meaningful chance to prevent compromise even if:
• The email bypasses the SEG
• The link arrives via social media or collaboration tools
• The site only becomes malicious after the message is delivered
2. Contextual and Behavioral Insight for SecOps
The endpoint is a rich telemetry source. When combined with phishing and link visibility, it gives SecOps a much deeper view of risk.
Endpoint phishing protection can:
• Track anonymized click behavior to spot unusual patterns
• Correlate source, timing, and propagation of phishing campaigns
• Reveal how a single malicious link spreads across teams, locations, or business units
This context helps security teams:
• Prioritize real threats instead of drowning in false positives
• Identify users or roles with higher exposure
• Tailor training and controls to actual attack patterns instead of generic risks
It also opens the door to automated, personalized training driven by real-world exposure—not hypothetical simulations.
3. Seamless User Experience, Not Security Friction

Employees are already under pressure to move fast. Security that constantly blocks or interrupts them gets ignored, bypassed, or disabled.
Well-designed endpoint phishing protection:
• Uses subtle, intuitive visual cues (like green/yellow/red badges)
• Provides inline guidance at the moment of the click
• Minimizes disruptive pop-ups or hard blocks unless truly necessary
This approach lets users stay productive while still being part of the security posture. A green "all clear" can give them confidence, while yellow or red warnings help them pause and think—without forcing them to become security experts.
At the same time, SecOps benefits from:
• Fewer noisy "suspected phishing" reports
• Better-quality alerts focused on real malicious link exposure
• Stronger coverage across email, web, social, and collaboration channels
Why Existing Tools Aren't Enough

Email gateways and network tools are critical—but they are not designed to win the modern phishing war by themselves.
Most of them rely on:
• Signatures of known bad domains and URLs
• Static rules and heuristics
• Periodically updated threat intelligence feeds
Attackers know this. They use:
• Polymorphic phishing links that change appearance
• Zero-day infrastructure that hasn't yet been blacklisted
• Delayed activation, where a link is benign at scan time and malicious later
• Compromised but trusted domains, which pass traditional reputation checks
When these campaigns slip through, your only remaining defense is what happens at the endpoint when a user interacts with the link.
Endpoint phishing and malicious link management provide:
• Adaptive, real-time analysis, not just pre-known signatures
• Protection across every digital channel, not just corporate email
• Immediate blocking even after the attack has bypassed other layers
Strengthening Your Security with Endpoint Phishing Protection
Phishing and malicious link attacks are constant, adaptable, and increasingly spread across channels your traditional tools don't fully cover. By adding phishing protection and malicious link management at the endpoint level, enterprises can:
• Reduce successful phishing compromises
• Shorten detection and response times
• Improve user confidence and reduce friction
• Feed richer intelligence back into the entire security stack
In a digital-first world, the question is no longer:
"Can we afford another security tool?"
It's:
"Can we afford to let users click without real-time protection?"
Meet PHISH360: Endpoint-First Phishing Protection
PhishCloud's PHISH360 is a dedicated point solution for endpoint phishing protection and malicious link management. It's designed to follow users across email, web, social, and collaboration tools—analyzing and scoring every link in real time.
If you're ready to secure the last mile of phishing defense—the click itself—it's time to bring protection directly to the endpoint.
Learn More About PHISH360🛡️ The Last Line of Defense
When email gateways and firewalls fail, the endpoint is where phishing attacks are won or lost.
Key Takeaways
Phishing Attacks Bypass Traditional Perimeters
With 2.6B phishing interactions and attacks delivered via social media, search ads, and collaboration tools, email gateways aren't enough.
Endpoint Protection Closes the Critical Gap
Real-time link scanning, unshortening, and dynamic analysis at the endpoint provide the last line of defense when other layers fail.
PHISH360 Delivers Endpoint-First Security
PhishCloud's PHISH360 follows users across every channel, analyzing links in real time with subtle visual cues and deep behavioral insights.
Meet PHISH360: Endpoint-First Phishing Protection
PhishCloud's PHISH360 is a dedicated point solution for endpoint phishing protection and malicious link management. It's designed to follow users across email, web, social, and collaboration tools—analyzing and scoring every link in real time.
If you're ready to secure the last mile of phishing defense—the click itself—it's time to bring protection directly to the endpoint.
Learn More About PHISH360